Theory vs. Practice
Diagnosis is not the end, but the beginning of practice.
G-WAN's Value: 450x Faster, and C/C++/JS/PHP are Legal again (made "memory-safe")
Does security finally matter? PHP and JS (written in C/C++ and not "memory-safe") are endangered by an executive order:
US President Joe Biden's administration wants software developers to use memory-safe programming languages and ditch vulnerable ones like C and C++.
Only Rust (funded by the GAFAM) would be allowed (due to international regulations) despite Rust created with C/C++, Rust not being really "memory-safe" (search for "memory"), and Rust relying on memory-unsafe OS syscalls written in (you guessed it)C/C++.
Under the flawed logic of ever-stretched fallacies justifying administrative transfers of wealth from the masses to a few ever-growing industry players, this ban should include everything written in C/C++ (Rust, Windows, OSX, Linux, Android, all Web browsers, Java, JS, PHP, OpenSSL, NGINX, etc.) – and almost everything written by everyone for the past 50 years.
Only G-WAN+SLIMalloc have escaped this trap: G-WAN and its servlets are "memory-safe", an objective security criteria.
The number of vulnerabilities is also an objective code-quality indicator (from the U.S. gov. database of vulnerabilities):
NGINX: 248 vulnerabilities (since 2004, click the link for the current count of CVEs, Common Vulnerabilities and Exposures)
G-WAN: 0 vulnerabilities (since 2009)
This is despite G-WAN JIT scripted servlets (since 2009) which immensely enlarge the surface of vulnerability as compared to NGINX, that only started recently to add basic scritping to generate dynamic contents (via slow IPC/inter-process communication instead of loading the language runtimes like G-WAN – which is much faster, but far more difficult to do safely).
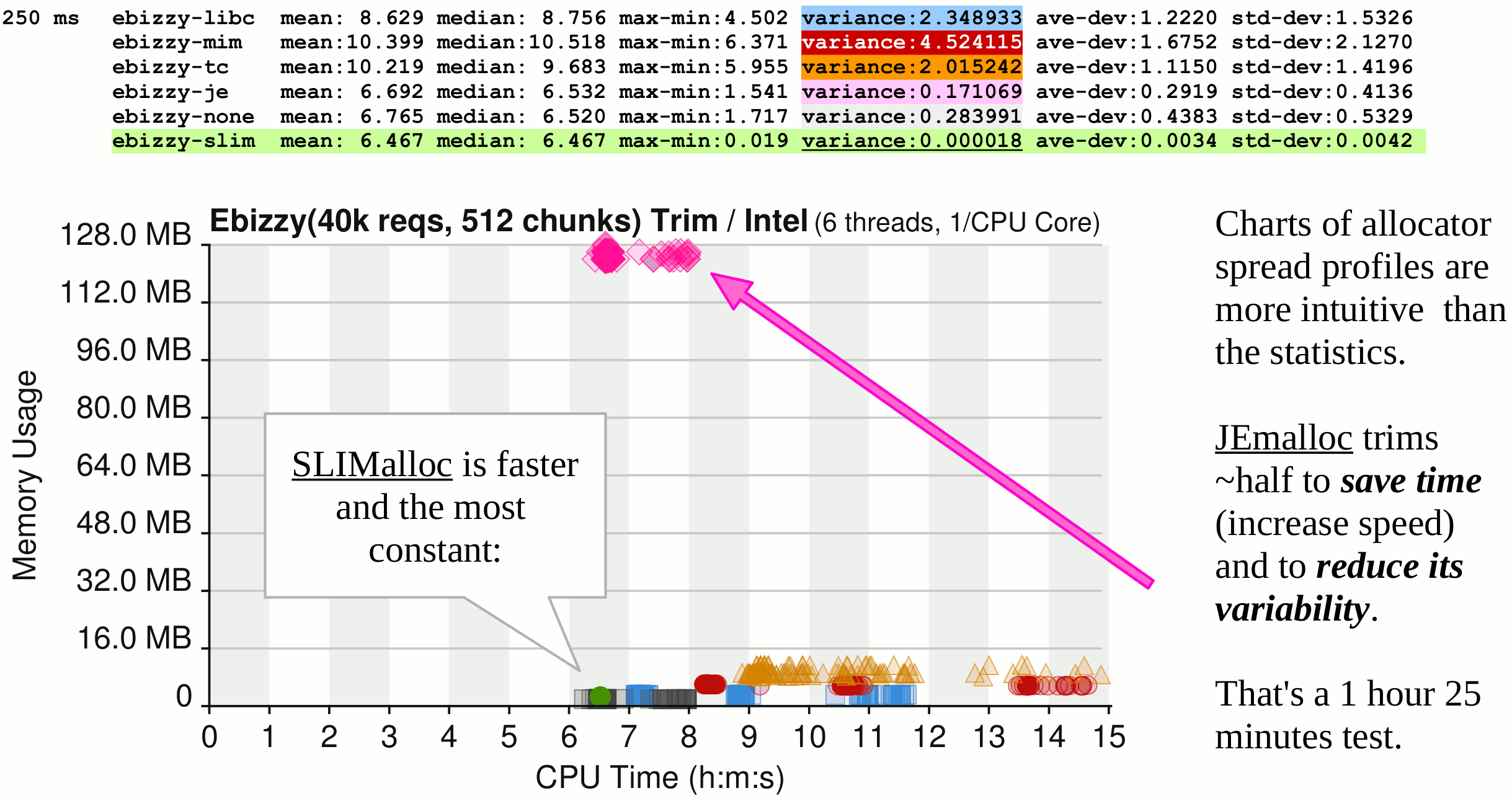
That was for 2009-2020 when G-WAN and NGINX relied on the same GLibC that SLIMalloc has proved, in graphic details, so unsafe (yet, surprisingly, a bit safer than Microsoft MIMalloc, Google TCmalloc, and Facebook/Meta JEmalloc which, don't ask me why, neglect to do the very basic checks done by the... 38-year old GLibC).
A clear past CVE record is a notable feat for a Web Application Server, but adding some sustainable certainty is certainly better:
SLIMalloc (a memory allocator) secures G-WAN, its servlets, and the loaded languages runtimes and libraries by:
(1) not introducing memory-allocation vulnerabilities (unlike all others),
(2) checking if accessed memory is under/over-written (all others don't bother),
(3) blocking and reporting memory-violations – without crashing the program (yet another exclusivity).
SLIMalloc (2020-2023) makes G-WAN safer than NGINX – and even safer than the so-called "memory-safe" languages (including Rust, which itself already had memory-safety vulnerabilities) because, unlike SLIMalloc, Rust flatly ignores the memory-violations originating from the OS (usermode and kernel) and third-party libraries... written in C/C++.
This is G-WAN's objective, heavily tested security published on ResearchGate – a clear improvement of the "State of the Art":
...immediately censored by Microsoft (my LinkedIn account is 'suspended' so it's invisible to all, and logging-in works but then access is denied: I have provided many times the requested ID without ever seeing any follow-up) but also censored on Wikipedia by the CTO a 'top of the line' Facebook and U.S. DoD Cyber-Security contractor (hiding his identity behind several fake accounts).
Now G-WAN's security has been explained, let's focus on objective reproductible performance. And, to make sure that G-WAN would not be criticized for having done cherry-picking (like others), we have used wrk2, a slower, more accurate version of the wrk benchmark written by... the NGINX team.
Why is wrk2 any better than wrk to accurately measure performance?
wrk sends a new request only after it has handled a server reply. By not tracking its own request rate, wrk fails to report slow, high-latency server replies. This is what the wrk2 author has properly named wrk client and NGINX server's "Coordinated Omission". Servers can't reply faster than the speed at which clients send their requests, and all the clients I have seen are G-WAN's bottleneck.
With G-WAN v17.2.7, wrk requires days to run a single "wrk -t10k -c10k http://127.0.0.1/100.html" test run... because wrk is unable to swiftly process the 242m G-WAN RPS.
The same NGINX v1.24.0 test runs in 10 seconds because wrk can handle the tiny 550k NGINX RPS on time. With such a tiny number of concurrent server replies, the slow wrk client does not need days.
In contrast, wrk2 sends requests at the user-supplied constant rate to the server (which will fail with I/O errors when overwhelmed). And wrk2 calibrates threads for 10 seconds (versus wrk's 0.5 second). The result is slower RPS scores than wrk, albeit more correct RPS and latency reports.
Since wrk2 sends requests at a constant-rate (unlike wrk which waits for having handled server replies to send new requests), wrk2 will stop the test after 10 seconds, not days – even with G-WAN (which is much, much faster than wrk and wrk2).
To test a 3-9 Watts MiniPC with a 4-Core ARM CPU and 16 GB RAM, wrk and wrk2 proved inadequate (either using too much RAM and agonizingly slow, or just lacking any real concurency) and therefore always G-WAN's bottleneck.
And beyond their asthmatic speed with high concurrencies, the wrk and wrk2 gargantuan memory usage (beheaded by the kernel OOM kill-switch) prevents from making tests on high concurrencies, simply because most machines (like this 16 GB MiniPC) don't have enough RAM! To illustrate the problem, we compared 2 ways of using wrk2, on our powerful i9-13900K PC with 192 GB RAM:
In our prior tests, wrk2 used 1 thread per connection to get more concurrency (result: G-WAN 281m RPS, NGINX 944k RPS):
wrk2 -c1 -t1 -R500m "http://127.0.0.1:80/100.html" wrk2 -c100 -t100 -R500m "http://127.0.0.1/100.html" wrk2 -c1k -t1k -R500m "http://127.0.0.1/100.html" wrk2 -c10k -t10k -R500m "http://127.0.0.1/100.html" wrk2 -c20k -t20k -R500m "http://127.0.0.1/100.html" wrk2 -c30k -t30k -R500m "http://127.0.0.1/100.html" wrk2 -c40k -t40k -R500m "http://127.0.0.1/100.html" (wrk2 uses 190 GB RAM, G-WAN 668 MB)
But in these tests targeting wrk2, 1 thread per Core was used, as NGINX does it (result: G-WAN 2m RPS, NGINX 1m RPS):
wrk2 -c1 -t1 -R500m "http://127.0.0.1/100.html" wrk2 -c100 -t32 -R500m "http://127.0.0.1/100.html" wrk2 -c1k -t32 -R500m "http://127.0.0.1/100.html" wrk2 -c10k -t32 -R500m "http://127.0.0.1/100.html" wrk2 -c20k -t32 -R500m "http://127.0.0.1/100.html" wrk2 -c30k -t32 -R500m "http://127.0.0.1/100.html" (wrk2 uses little RAM, at low concurencies) ... wrk2 -c100k -t32 -R500m "http://127.0.0.1:80/100.html"
Since G-WAN reached 281m RPS (NGINX 944k) with wrk2 using many threads, it is obvious that the G-WAN bottleneck is wrk2:
G-WAN cannot serve requests faster than sent by the wrk2 client.
This also explains why NGINX is not able to handle high concurrencies:
|
NGINX forces people to wait for their turn (in each per-process/thread event-based queue, only one person can embark at any given time). The more CPU Cores and processes/threads, the higher the CPU and RAM overheads – and the wait times for the people queuing to embark. |
G-WAN lets tens of thousands of people travel together (each thread lets hundreds of thousands of people make a step forward altogether). The more CPU Cores and threads, the lower the CPU and RAM overheads – and the latency between steps. |
These tests have demonstrated that G-WAN is much faster (and using less RAM at a given concurrency-level) than both wrk2 and NGINX (based on the same flawed design and implementation)... but also that a G-WAN-based benchmark tool is required to report its real performance.
That's how G-WAN performance is objectively measured and reproduced (scientists create and use benchmarks for a reason). Using the wrk2 NGINX testing tool on localhost or a LAN is "not the real world": it lacks the large Internet network latencies and users reading a page before visiting another page.
So, if you let G-WAN using Internet-sized timeouts then it will handle idle connections just like NGINX (which also has to use proper timeout values). Claiming that NGINX is able to stack more idle connections than G-WAN is false – unless you set NGINX with a large timeout and G-WAN with a small one, to force it close idle connections earlier.
When vendors revert to fallacies (after far more informative comparisons were furiously censored), that's not a good sign:
- NGINX "capability to handle many connections simultaneously" (944k for NGINX versus 281m for G-WAN...)
- "NGINX has a strong security track record" (with hundreds of vulnerabilities versus... zero vulnerabilities for G-WAN!)
- the "steeper [G-WAN] learning curve" (despite a zero-conf. G-WAN – compare that to the arcane NGINX configuration files)
- "G-WAN is a high-performance web server focusing on C scripts" (C and 17 other programming languages: JS, C#, PHP, Java...)
- "G-WAN primarily focuses on C/C++, but with certain tweaks, other languages might be executed" (the "tweaks" are just to install the language runtimes – then you can "edit and play" G-WAN servlets without any configuration!)
NGINX lacks G-WAN's (1) "edit and play" servlets in 18 programming languages and (2) "edit and play" contents/protocol handlers. So G-WAN developers can port NGINX modules to G-WAN – but NGINX has yet to offer anything close to G-WAN's "edit and play" servlets and handlers.
That was a long introduction – as I have for the first time (in my blog) presented the technical arguments before the question.
So, what was the question?
How to Write About G-WAN (How-To with objective metrics and official references)
The technical arguments (security, performance) are listed above. Below, many official "memory-safety" references are listed – just in case you need to (1) read about it from another perspective (mainly stating that there's no silver bullet), or (2) to show your boss or investors that this is a real and serious problem (something that, after six decades of denial and censorship, is finally officially confirmed by several U.S. government agencies as mandatory to secure the U.S. critical infrastructure and the U.S. economy):
- https://www.whitehouse.gov/wp-content/uploads/2022/09/M-22-18.pdf
- https://media.defense.gov/2023/Apr/27/2003210083/-1/-1/0/CSI_SOFTWARE_MEMORY_SAFETY_V1.1.PDF
- https://media.defense.gov/2023/Dec/06/2003352724/-1/-1/0/THE-CASE-FOR-MEMORY-SAFE-ROADMAPS-TLP-CLEAR.PDF
- https://www.cisa.gov/sites/default/files/2023-12/CSAC_TAC_Recommendations-Memory-Safety_Final_20231205_508.pdf
- https://bidenwhitehouse.archives.gov/wp-content/uploads/2024/02/Final-ONCD-Technical-Report.pdf
- https://cyberdefensereview.army.mil/Portals/6/Documents/2024-Fall/Yarbrough_Guan_CDRV9N3-Fall-2024.pdf
- https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=958266
- https://web.mit.edu/ha22286/www/papers/CACM25.pdf
- https://www.ic3.gov/CSA/2025/250212.pdf
The market players, their motivations, and the "unstoppable march of progress"
For commercial reasons (profit, marketshare, infinite growth required to pay-back an ever-growing debt), the GAFAM slowly make progress in "memory-safety" security (while performance slightly decreases and the number of OS patches explodes).
Yet what they do for Rust is not done for C or C++ (Bjarne noticed it and is now copying Rust's memory-safety in an attempt to save C++ from a regulatory ban – given the size and complexity of the animal, that will not be an easy task).
So, SLIMalloc is the only usable option for C/C++ (the OS, and the popular languages derived from the C/C++ runtimes, like C#, D, Go, Java, Javascript, Lua, Objective-C, Perl, PHP, Python, Ruby, Scala, etc.).
The level of required skills to resolve these (security and multicore) problems will let very few Web servers (and even less App. servers) stay (legally, technically and financially) viable options on the global market.
The foreseeable outcomes
This situation will probably benefit to G-WAN – because:
- from 2009 to 2025, G-WAN has consistently been much faster (and safer) than anything else;
- G-WAN+SLIMalloc will save C/C++/JS/Java/PHP their authors and developers from oblivion;
- less market players will allow end-users better evaluate the competiting products and vendors;
- as time goes – and while the number of CPU Cores grows – G-WAN scales increasingly better;
- AI, Crypto mining, and today's 50BN connected objects (car, watch, TV, smartphone, computer);
- the IoT is expected to grow from 50bn to 100bn connected objects by 2030 (twice the telemetry);
- the rise of the energy prices and of their associated regulatory constraints will pressure everyone;
- the ever-accelerating monetary-mass growth has stopped and will slow-down, restoring parsimony;
- TWD, which I founded in 1998 and that sells G-WAN, has a background of fantastic achievements.
The future looks much brighter to me than the past. I am not sure that our competitors can claim the same.